










If you are using Trusted Oracle7 in DBMS MAC mode, your DBMS label must dominate the creation label of the users whose SQL statements you are auditing.
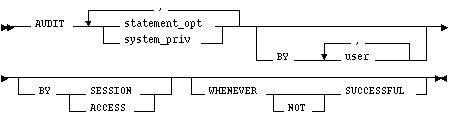
statement_opt
chooses specific SQL statements for auditing. For a list of these statement options and the SQL statements they audit, see Table 4 - 7 and Table 4 - 8.
system_priv
chooses SQL statements that are authorized by the specified system privilege for auditing. For a list of all system privileges and the SQL statements that they authorize, see Table 4 - 11.
BY user
BY SESSION
BY ACCESS
causes Oracle7 to write one record for each audited statement.
If you specify statement options or system privileges that audit Data Definition Language statements, Oracle7 automatically audits by access regardless of whether you specify the BY SESSION or BY ACCESS option.
For statement options and system privileges that audit other types of SQL statements, you can specify either the BY SESSION or BY ACCESS option. BY SESSION is the default.
WHENEVER SUCCESSFUL
chooses auditing only for SQL statements that complete successfully.
NOT chooses auditing only for statements that fail, or result in errors.
If you omit the WHENEVER clause, Oracle7 audits SQL statements regardless of success or failure.
Enable auditing: You must enable auditing with the initialization parameter AUDIT_TRAIL.
Specify auditing options: To specify auditing options, you must use the AUDIT command. Auditing options choose which SQL commands, operations, database objects, and users Oracle7 audits. After you specify auditing options, they appear in the data dictionary. For more information on data dictionary views containing auditing options see the "Data Dictionary" chapter of Oracle7 Server Reference.
You can specify auditing options regardless of whether auditing is enabled. However, Oracle7 does not generate audit records until you enable auditing.
Auditing options specified by the AUDIT command (SQL Statements) apply only to subsequent sessions, rather than to current sessions.
CONNECT
This short cut is equivalent to specifying the CREATE SESSION system privilege.
RESOURCE
This short cut is equivalent to specifying the following system privileges:
DBA
ALL
This short cut is equivalent to specifying all statement options shown in Table 4 - 7, but not the additional statement options shown in Table 4 - 8.
ALL PRIVILEGES
This short cut is equivalent to specifying all system privileges.
Oracle Corporation encourages you to choose individual system privileges and statement options for auditing, rather than these short cuts. These short cuts may not be supported in future versions of Oracle.
Statement Option
SQL Statements and Operations
ALTER SEQUENCE
ALTER SEQUENCE
ALTER TABLE
ALTER TABLE
COMMENT TABLE
COMMENT ON TABLE table, view, snapshot
COMMENT ON COLUMN table.column, view.column, snapshot.column
DELETE TABLE
DELETE FROM table, view
EXECUTE PROCEDURE
Execution of any procedure or function or access to any variable or cursor inside a package.
GRANT PROCEDURE
GRANT privilege ON procedure, function, package
REVOKE privilege ON procedure, function, package
GRANT SEQUENCE
GRANT privilege ON sequence REVOKE privilege ON sequence
GRANT TABLE
GRANT privilege ON table, view, snapshot.
REVOKE privilege ON table, view, snapshot
INSERT TABLE
INSERT INTO table, view
LOCK TABLE
LOCK TABLE table, view
SELECT SEQUENCE
Any statement containing sequence.CURRVAL or sequence.NEXTVAL
SELECT TABLE
SELECT FROM table, view, snapshot
UPDATE TABLE
UPDATE table, view
Table 4 - 8. Additional Statement Auditing Options
Example I
AUDIT ROLE
To choose auditing for every statement that successfully creates, alters, drops, or sets a role, issue the following statement:
AUDIT ROLE
WHENEVER SUCCESSFUL
To choose auditing for every CREATE ROLE, ALTER ROLE, DROP ROLE, or SET ROLE statement that results in an Oracle7 error, issue the following statement:
AUDIT ROLE
WHENEVER NOT SUCCESSFUL
Example II
To choose auditing for any statement that queries or updates any table, issue the following statement:
AUDIT SELECT TABLE, UPDATE TABLE
To choose auditing for statements issued by the users SCOTT and BLAKE that query or update a table or view, issue the following statement:
AUDIT SELECT TABLE, UPDATE TABLE
BY scott, blake
Example III
To choose auditing for statements issued using the DELETE ANY TABLE system privilege, issue the following statement:
AUDIT DELETE ANY TABLE
![[*]](jump.gif) NOAUDIT (SQL Statements) command
NOAUDIT (SQL Statements) command ![[*]](jump.gif)




